Firewalls and Ports
All services must be listening on the appropriate ports. Most monitoring systems provide a means of testing whether a given port is accepting connections and service-specific tools may also be available. In addition, the generic system tool Telnet can also be used to initiate the connection:
telnet HOST_NAME PORT
Note
Standalone
The following sections describe the ports that are required by the Chef Infra Server in a standalone configuration:
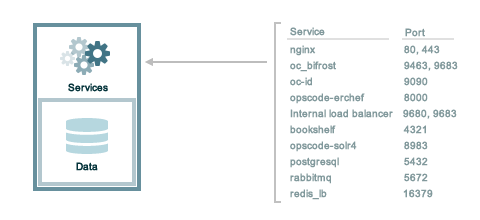
127.0.0.1
address. This ensures that all of the services are available to the Chef
Infra Server, in the event that the Chef Infra Server attempts to
contact itself from within a front or back end machine. All ports should
be accessible through the loopback interface of their respective hosts.For a standalone installation, ensure that ports marked as external
(marked as yes in the External column) are open and accessible via
any firewalls that are in use:
| Port | Service Name, Description | External |
|---|---|---|
4321 | bookshelf The bookshelf service is an Amazon Simple Storage Service (S3)-compatible service that is used to store cookbooks, including all of the files—recipes, templates, and so on—that are associated with each cookbook. | no |
80, 443, 9683 | nginx The nginx service is used to manage traffic to the Chef Infra Server, including virtual hosts for internal and external API request/response routing, external add-on request routing, and routing between front- and back-end components.Note Port 9683 is used to internally load balance the oc_bifrost service. | yes |
9463 | oc_bifrost The oc_bifrost service ensures that every request to view or manage objects stored on the Chef Infra Server is authorized. | |
9090 | oc-id The oc-id service enables OAuth 2.0 authentication to the Chef Infra Server by external applications, including Chef Supermarket. OAuth 2.0 uses token-based authentication, where external applications use tokens that are issued by the oc-id provider. No special credentials—webui_priv.pem or privileged keys—are stored on the
external application. | |
8000 | opscode-erchef The opscode-erchef service is an Erlang-based service that is used to handle Chef Infra Server API requests to the following areas within the Chef Infra Server:
| |
5432 | postgresql The postgresql service is used to store node, object, and user data. | |
9200 | elasticsearch The elasticsearch service is used to create the search indexes used for searching objects like nodes, data bags, and cookbooks. (This service ensures timely search results using the Chef Infra Server API; data that is used by the Chef platform is stored in PostgreSQL.) | |
16379 | redis_lb Key-value store used in conjunction with Nginx to route requests and populate request data used by the Chef Infra Server. Note From Chef Infra Server version 15.10.12 onwards, we are using keydb instead of redis underneath. All the functions are supposed to work the same because keydb is a fork of redis. The configuration name and service name will continue to be redis_lb. |
Tiered
The following sections describe the ports that are required by the Chef Infra Server in a tiered configuration:
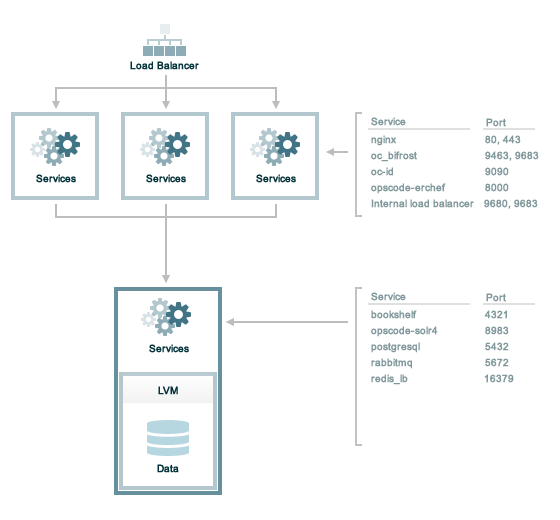
127.0.0.1
address. This ensures that all of the services are available to the Chef
Infra Server, in the event that the Chef Infra Server attempts to
contact itself from within a front or back end machine. All ports should
be accessible through the loopback interface of their respective hosts.Front End
For front-end servers, ensure that ports marked as external (marked as
yes in the External column) are open and accessible using any
firewalls that are in use:
| Port | Service Name, Description | External |
|---|---|---|
80, 443, 9683 | nginx The nginx service is used to manage traffic to the Chef Infra Server, including virtual hosts for internal and external API request/response routing, external add-on request routing, and routing between front- and back-end components.Note Port 9683 is used to internally load balance the oc_bifrost service. | yes |
9463 | oc_bifrost The oc_bifrost service ensures that every request to view or manage objects stored on the Chef Infra Server is authorized. | |
9090 | oc-id The oc-id service enables OAuth 2.0 authentication to the Chef Infra Server by external applications, including Chef Supermarket. OAuth 2.0 uses token-based authentication, where external applications use tokens that are issued by the oc-id provider. No special credentials—webui_priv.pem or privileged keys—are stored on the
external application. | |
8000 | opscode-erchef The opscode-erchef service is an Erlang-based service that is used to handle Chef Infra Server API requests to the following areas within the Chef Infra Server:
|
Back End
For back-end servers in a tiered Chef Infra Server installation, ensure
that ports marked as external (marked as yes in the External
column) are open and accessible using any firewalls that are in use:
| Port | Service Name, Description | External |
|---|---|---|
80, 443, 9683 | nginx The nginx service is used to manage traffic to the Chef Infra Server, including virtual hosts for internal and external API request/response routing, external add-on request routing, and routing between front- and back-end components.Note Port 9683 is used to internally load balance the oc_bifrost service. | yes |
9463 | oc_bifrost The oc_bifrost service ensures that every request to view or manage objects stored on the Chef Infra Server is authorized. | |
9200 | elasticsearch The elasticsearch service is used to create the search indexes used for searching objects like nodes, data bags, and cookbooks. (This service ensures timely search results using the Chef Infra Server API; data that is used by the Chef platform is stored in PostgreSQL.) | |
5432 | postgresql The postgresql service is used to store node, object, and user data. | |
16379 | redis_lb Key-value store used in conjunction with Nginx to route requests and populate request data used by the Chef Infra Server. Note From Chef Infra Server version 15.10.12 onwards, we are using keydb instead of redis underneath. All the functions are supposed to work the same because keydb is a fork of redis. The configuration name and service name will continue to be redis_lb. | |
4321 | bookshelf The bookshelf service is an Amazon Simple Storage Service (S3)-compatible service that is used to store cookbooks, including all of the files—recipes, templates, and so on—that are associated with each cookbook. | |
8000 | opscode-erchef The opscode-erchef service is an Erlang-based service that is used to handle Chef Infra Server API requests to the following areas within the Chef Infra Server:
|